What Makes AudioOne Conference Calling Different? Security
What is the main reason enterprise companies prefer phone line conference calling over internet connections? Reliability.
With a different infrastructure, phone lines aren’t susceptible to the same outages as the internet, often making traditional conferencing much more desirable than VoIP.
What people don’t realize is that conference calls also can offer greater security. In a world constantly threatened by hackers and call snoopers, organizations around the globe need to feel confident in their conference call security.
Whether you’re discussing quarterly revenue figures during an executive meeting or sharing results from recent medical research trials, making sure your information isn’t compromised by some call snooper – or accidentally leaked – is essential. (Learn more about the threats to your calls in this blog.)

That’s why MeetingOne continues to prioritized secure conference calling while other audio conferencing providers are rolling back protection to cut their costs. Some providers are even sacrificing security to meet the demand to make calls easier to access!
At MeetingOne, we believe in providing top-notch security while maintaining quick call access at competitive prices.
AudioOne, MeetingOne’s premier conference calling service, has a diverse set of security features critical to our customers. We help clients across industries remain compliant with local and federal laws when sharing sensitive information during conference calls. A research agency that’s part of the US government, for example, couldn’t operate as efficiently without MeetingOne’s conference call security.
In this blog, we’ll share one of the most important factors that differentiates MeetingOne from other providers: Security.
4 Aspects of AudioOne’s Conference Call Security
AudioOne is loaded with tiers of security features intended to help protect your calls. And many of these features work in “the background.” Contrary to expectations, easy access to calls is entirely possible even with strong security measures in place!
These features are set up in two of our MeetingOne platforms: Our Online Account Management (OAM) portal, and our call interface, Click&Meet. OAM provides users access to all things relevant to their calls. Click&Meet is an intuitive computer interface that lets you manage your calls with your mouse. We’ll dig into each platform at later points in the blog.
Let’s explore four factors that define AudioOne’s conference call security: Administrative Controls, Access Features, Click&Meet & Recordings. (Click on the topic that most interests you!)
.
#1. Administrative Controls in OAM
OAM (or Online Account Management) is a portal where users have access to call reports and recordings, contact info and security features. There are two tiers of security settings that are dependent on a user’s role within OAM.
Most AudioOne users are Room Hosts in OAM, and they have specific options for securing their audio rooms. The other category is Account Administrator, and these users can manage room settings for all Room Hosts across a company.
Let’s dig into both!
Room Hosts
Room Hosts have an array of “In Call” settings they can manage.
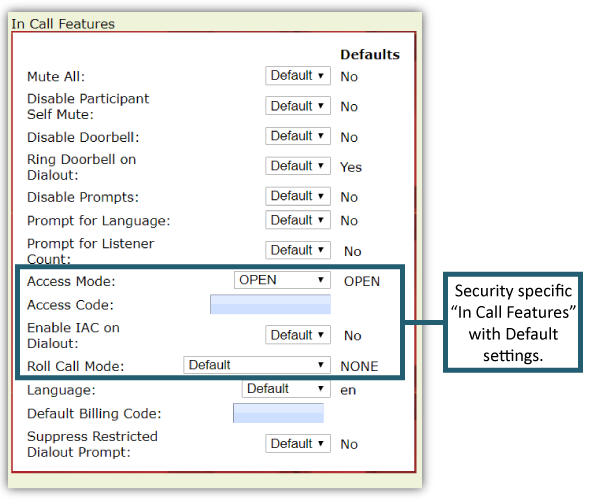
Many are essential for conferencing call security, including the following examples.
Access Mode
Participant access to conference calls can be preset in OAM for users’ audio rooms. The settings are easy to adjust. By simply selecting a drop-down menu, you can choose between several access options: Open, Locked, Code, IAC, Code_IAC or Screened.
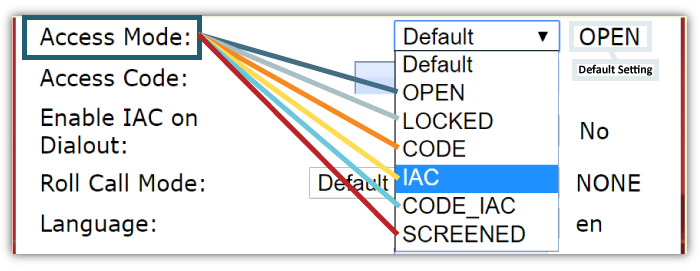
These options give users various levels of security strength. Obviously, an Open audio room is accessible to anyone, and once Locked, entrance is prohibited.
Using a “Code” (Access Code) gives you an opportunity to secure the room with one password everyone has to use. This is an ideal option for one-off events. If you need to host an emergency call, for example, you can require everyone to use a code you create on the spot. People without that code simply won’t be able to get in; thus avoiding unwanted listeners.
Individual Access Codes (“IAC”), on the other hand, allow access to those participants with a unique code per individual. It’s great for identifying participants attending recurring events open to larger numbers of people within your organization. Our conferencing bridge recognizes all the IACs your company has stored, so it makes it easy to identify people within your company and allow them access to these calls, without accidentally exposing yourself to call snoopers.
Using “Code_IAC” is a great way to layer security with both IACs and Access Codes.
And “Screened” automatically sends attendees to the Waiting Lounge, where the Host may allow them into the main call one-by-one. Great for small calls with a dozen participants or fewer. Not ideal for conferences with hundreds or thousands of callers. 😉
(We will look further into all of these Access Modes later in the blog.)
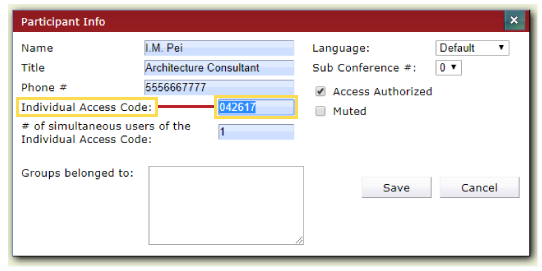
Participant Info
OAM allows you to add contacts and their information to a Directory within the system. When creating new contacts, Room Hosts are prompted to set up Individual Access Codes. This ensures a baseline level of security.
The opportunities to increase security go further, though. Worried an individual may be “too eager” when participating and reveal something confidential? Check the “Muted” checkbox – and they will be muted when joining the call by default.
Want them to be able to access certain calls but not others? Select or deselect the “Access Authorized” checkbox prior to a call. If not selected, a caller can’t accidentally stumble into a call they weren’t invited to attend. The last thing you want is someone without the right clearance being privy to an important call.
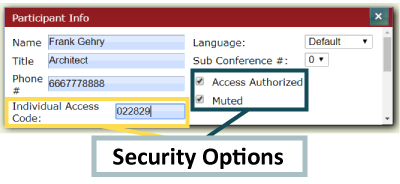
Establishing these security measures early is simple and effective.
Roll-Call
Many features in OAM serve dual purposes. Take the option to require a Roll-Call. It serves the simple job of announcing attendees as they join the conference call. We’ve all been on those calls where people join but don’t inform the rest of us they are present. Roll-Call eliminates that annoyance!
Being announced during the call also functions as a security measure. With each person naming themselves, Room Hosts can feel more confident they know who is joining. If you hear a name that doesn’t sound familiar, you can take steps to determine who they are – friend or foe.
Account Administrators
Administrators can set general room settings for all AudioOne users in their account. Many of the features they adjust factor into room security. All you have to do to setup company wide room settings is select the “Rooms” tab and toggle the “Default Settings.” Defining these settings is a great way to increase security without impacting ease-of-access to calls.
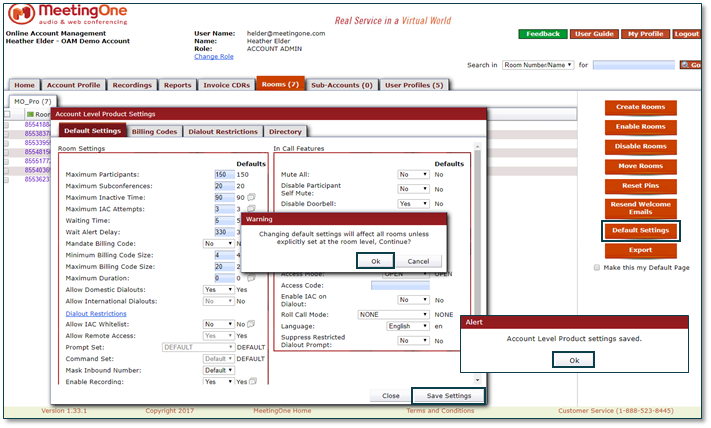
Here are a few examples of settings you can employ to bolster your conference call security.
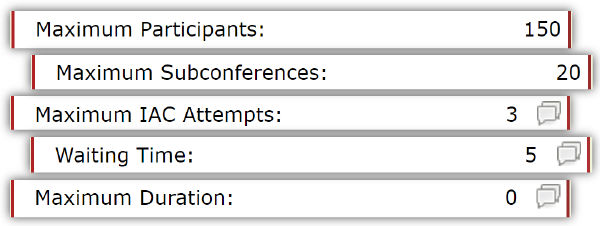
Maximum Participants
In OAM, Account Administrators can predetermine the max number of participants in rooms across the organization. The research organization we mentioned in the intro is a prime example of a group that could benefit from this feature.

They mainly hold calls that consist of 12 or fewer participants. These calls facilitate conversations between doctors and researchers about the latest medical findings. Because these calls are extremely confidential, they have to eliminate all possibilities of unwanted participants.
By keeping the room number low, they could limit the number of people who enter. When that maximum number of participants show up, no one else can get in.
(Of course, setting the maximum number is dependent on your organization’s needs. Don’t think that because you set a max means you you’re stuck there. We’re flexible at MeetingOne, and we can take steps to help you increase room capacity as needed!)
Subconferences
While sub-conference rooms are terrific for holding breakout sessions and huddles, having too many can become a security issue. With AudioOne, your audio room has up to 20 sub-conference rooms to distribute call participants into as needed.
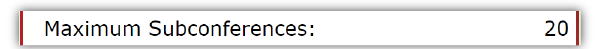
We would encourage you to use as many as needed, but we recognize that having too many can make it hard to keep track of participants. So, if you feel you need to better be able to monitor small group discussions for security reasons, you can limit the number of rooms available.
IAC Attempts
Limiting IAC attempts is one of the best conference call security features I think we offer. Admins can set the number of times someone can unsuccessfully use an IAC to join a call.
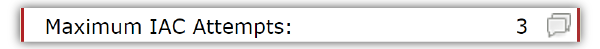
Why is this valuable? Let’s say you set the number at 3 attempts. Occasionally, an employee may accidentally input their code wrong. 3 attempts gives them a mulligan (or two). If someone can’t get it in 3 attempts, though, there’s the possibility they shouldn’t actually have access to the call at all.
Maybe it’s a snooper just testing numbers, hoping to get lucky. You wouldn’t want them to have an unlimited number of tries to sneak in. And if it turns out it was an employee with ten thumbs, AudioOne gives you other ways to ensure you get them on the call. You can also choose to be notified if one of your callers is having difficulties getting in, and assist them as needed.
Waiting Time
AudioOne gives you the option to set a cut off mark for how long someone can spend trying to get into a call. Once they’ve dialed in, the timer starts.

As with the IAC Attempts option, this tool is desirable for eliminating snoops who may be loitering in the Waiting Lounge, trying to break into the audio room.
Let’s consider this in real-life terms. How long does it take to input a Code? A minute? Two if you mess up? So, if someone’s just sitting in the waiting lounge for 10-15 minutes, either they are very confused about how to get it, or they potentially shouldn’t be on the call.
Maximum Duration
While Maximum Duration really is a cost-saving feature (helping you avoid racking up too many minutes), it could be repurposed as a security tool. The longer a conference goes, the more exposure it has to call snoopers, in theory.

Setting a Maximum Duration limits that window. Smaller window, lower susceptibility to unwanted visitors. (Zero is the default setting.)
Multiple Audio Rooms
AudioOne users can create multiple audio rooms in OAM to facilitate their conference calls. Depending on your needs, individual rooms could be formatted with more security features and others with fewer.
The value of this functionality is apparent. Some calls may require rigid security so the wrong folks can’t join. Others may be more lax, with a large audience that needs easy access.
One of our healthcare clients operates in a way similar to this. They hold “All Hands” calls every two weeks with an average of 1,000 participants. It’s important that joining the call is straightforward for attendees. They also hold weekly internal calls consisting of 100-200 callers. While still large, these calls may require more security to ensure HIPPA compliance.
.
#2. Access Features
Access is everything when it comes to conference call security. We mentioned a few examples above. We go into greater detail here.
Host Dial-Out
What’s the simplest access combination you can use to secure your conference calls? Host dial-out + a locked audio room.
It works like this. You set your Access Mode to “Locked” in OAM. Then, you jump into Click&Meet. You then start your conference call.

Using your directory feature – preloaded with contacts you added in OAM – you can select users and dial-out to them. AudioOne will then call those users. No one gets in without your directly contacting them.
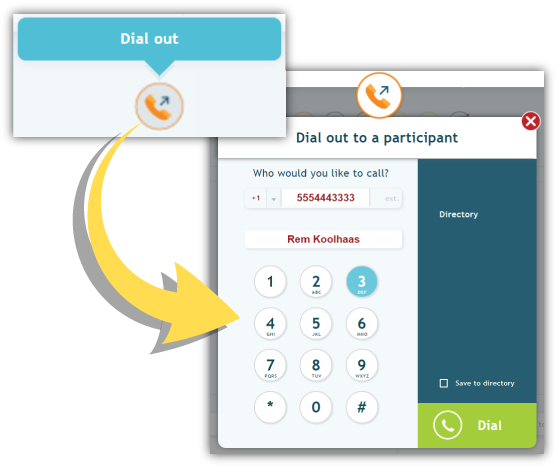
This method eliminates the need for access codes, but it does put the onus on you to make sure the right people are contacted.
That said, MeetingOne still gives you the option to require callers to input IACs when dialed out to – if that need arises. All you have to do is change “Enable IAC on Dialout” from the default “No” to “Yes.” Doubling down on security is always a safe bet!
IACs
Individual Access Codes (IACs) are at the heart of the AudioOne Security system! (And AudioOne’s identification processes, in general! OAM uses IACs to automatically identify callers as they connect with our conference call bridge.)
As the name suggests, IACs are codes given to individual participants when they are created as a contact in OAM or Click&Meet. (The two platforms are interconnected. Create a contact in the directory of either, and it will be available in both.) Each code is unique to that contact. The codes will automatically generate in OAM and Click&Meet if you do not add one when creating a contact.
For security purposes, IACs are highly desirable. If you set your audio room’s Access Mode to “IAC” (as mentioned above), callers must enter their particular code to join the call. You’ll know everyone who joins because their information will automatically be populated.
IACs can also be reported on after your call has concluded within OAM. Thanks to these individualized codes, you can get the full list of identified callers, no matter what phone number they choose to use to dial in with that day.
As a sub-category of access codes, IACs have an obvious value for conference call security. But given our IACs are part of the identification process, too, you’re doubling down on security in one fell swoop. Not only is it harder to get in, everyone joining will be named and recognizable in Click&Meet (more below). If someone appears who shouldn’t be on the call, you can disconnect them with two clicks of the mouse.
IACs are a terrific tool!
Access Codes
As mentioned above, Access Codes provide an alternative for your conference call security. Let’s think of IACs as the default, and Access Codes as a second option.
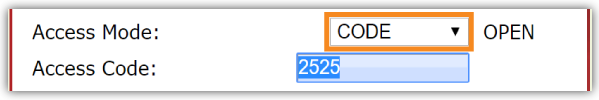
IACs are ideal for recurring conference calls with a defined set of participants. Each time they jump on the call, they use the same code.
But sometimes you must facilitate one-off calls with users from around the country (or globe). Conference Codes may prove a better option. You can set the Access Mode to “Code” and define a new code for that event, then you quickly inform callers of the code. This ensures your call will be secured by a unique code for that one event. (You will have to reset the Access Mode after the call to IAC.)
Layering Access Codes
The greater your conference call security needs are, the more you’ll benefit from layered access codes.
Layering codes in OAM is very simple. You first select the Access Mode option “Code_IAC” in Settings. Then you input a Code. Now, all participants must enter both the conference code AND their IAC to join the call. And you – as the Host – are completely in control of what that conference code is.
The value is apparent. By requiring two codes, you’re filtering out possible snoops and employees who may join. You can be confident that those on the call, were intended to be there.
.
#3. Click&Meet Call Interface
The final line of call security we offer comes in an unusual form: Our conference call visual management interface – Click&Meet. It’s another great example of a tool playing multiple roles.
Click&Meet was intended help Hosts manage large numbers of conference call participants from their computer. But Click&Meet also gives you the ability to screen participants as they come, isolate suspicious callers, or boot individuals who shouldn’t be in attendance. Using Click&Meet can be a boon to your conference call security.
Participant Control – Avatars
Call interfaces are awesome because they provide hosts a simple visual representation for callers: Avatars!
Avatars serve security purposes because they give hosts the option to select and mute, move or disconnect disruptive or unwanted callers. If I feel a caller is sharing inappropriate information, I can right-click and mute them within Click&Meet. Maybe they shouldn’t be in attendance. Same process to disconnect them.
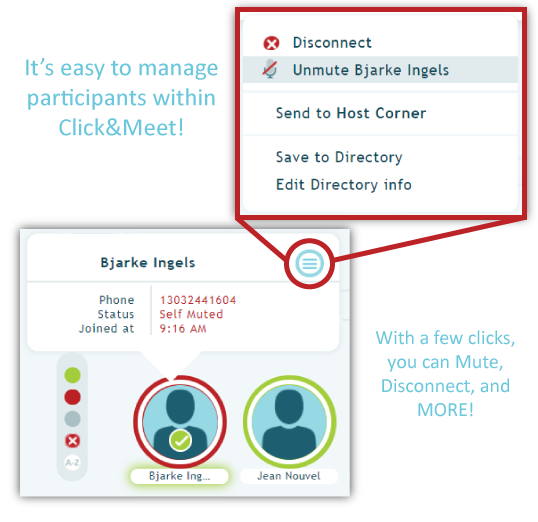
Being able to deal with one caller at a time is a huge benefit for Hosts using Click&Meet. It’s a fast, efficient way to deal with troublesome individuals.
(Callers with their name circled in GREEN are speaking; callers circled in RED are muted; callers not speaking are GREY.)
Host Corner – Screening
The Host Corner is a space apart from the main conference room where a host can talk to participants. Conversations held in the host corner won’t be heard in the main conference room.
Many of our customers use the Host Corner to screen incoming callers. Some hosts use it as an opportunity to greet participants. Some use the Host Corner to talk with Speakers before a call. Others still use it for security purposes – to filter out callers who shouldn’t be in attendance.
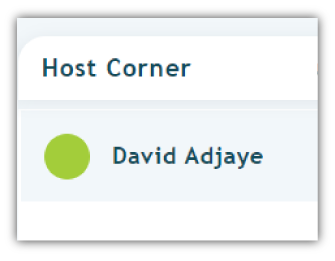
Using the host corner is a simple way to up security without making participant access more difficult. Callers that appear to be struggling to enter the room from the waiting lounge can easily be selected by hosts and brought into the Host Corner. There, they can be vetted and approved or denied. Simple and effective.
Muting
Believe it or not, the greatest threat to conference call security and the compromise of information isn’t your everyday hacker. It’s your everyday blabbermouth.
It’s true. Internal leaks are almost impossible to predict, and they can be the result of ignorance, rather than ill-intentions.
If you have a Joe Schmoe on your call who’s bringing up sensitive information that maybe he shouldn’t, with Click&Meet you can quickly mute him. And you can mute him without silencing your entire call audience. That’s a huge plus!
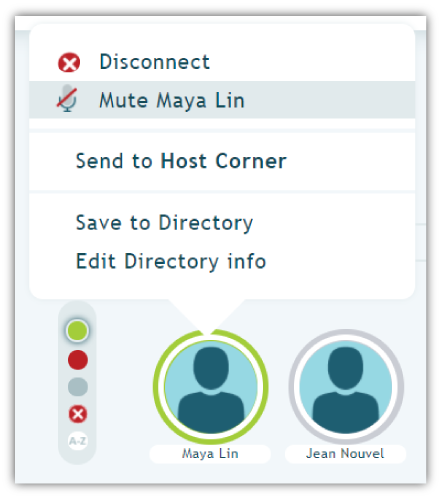
Disconnection
If you found out you had someone snooping on your call, what is the first thing you would want to do? Jot down what information you can get – likely name and number. Right after that, I would want to drop them from the call.
The challenge with disconnection is that some providers don’t make it is easy to drop just one caller. With Click&Meet, all you have to do is select their avatar, right-click, and disconnect.
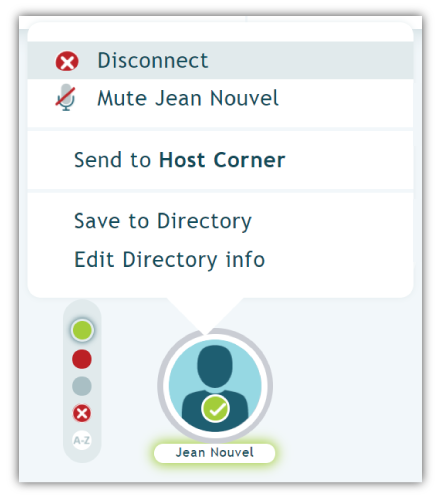
Disconnecting individual callers shouldn’t be a hassle. If your call provider only gives you the nuclear option – Disconnect All/End Conference – it may be time to move on from them.
Wait Alert Delay
We already spoke to setting a maximum Waiting Time in an above section. The Wait Alert Delay in Click&Meet is an ideal, repurposable tool for monitoring suspicious callers.
While it’s actually intended to help Hosts identify callers who may be struggling to enter, the Wait Alert Delay is also a handy security feature. You set the Delay for a certain number of seconds. Once a caller hits that number, their Avatar is flagged in the Waiting Lounge.
This gives the host a cue that person may be having troubles entering. With a simple click, hosts can move a person into the Click&Meet Host Corner, as discussed above.
Most callers that get flagged are folks merely having trouble getting in. But on the off-chance it’s not, it’s great for a host to be able to sequester a suspicious caller, identify them, and then drop them from the call if needed.
Admin Tip: Set your Wait Time Delay to correspond with your Wait Time limit. If you expect people to be able to enter within two minutes of dialing in, set the Delay to 120 seconds. Then set your Wait Time to give them a minute or two more.

You’ll get the notice they are struggling to enter. If it’s not a number you recognize, you can leave them in the cold until they are booted thanks to the Wait Time limit.
#4. Recordings
Conference call security doesn’t end with the call. Many organizations we work with have very specific needs surrounding their call recordings.
While it’s not often considered, protecting call recordings is an integral part of conference call security. Here are the ways we provide for our customers.
Ability to Record
The research agency we earlier referred to is an excellent example of an organization with specific recording needs. Given their discussions entail confidential information, they are not allowed to record their conference calls.
Of course, AudioOne provides users a straightforward option for recording calls. By simply selecting the record icon in Click&Meet – or using a dial pad command (51#) – the content of your calls will be recorded and saved. Or, you just don’t.
For this particular company, we had to go even further. They needed their own instance of Click&Meet to be ‘locked-in.’ This required us to custom develop a room with the recording feature completely “turned off” – which we were happy to accommodate!
Recording Storage and Transmission
The more significant issue with recordings tends to be their storage and transmission. Were a recording to be snapped up by a hacker while still in the hands of an audio conferencing provider, there would be hell to pay.
MeetingOne doesn’t mess around with call recordings. Whether in storage or transmission, we encrypt all recordings with AES-256 bit – among the top ciphers. AES has high enough “computational complexity” to be used by the US government to protect classified information.
We didn’t stop there. MeetingOne employs combinations of symmetric and asymmetric encryption to bundle recordings in layers of security. Symmetric and asymmetric encryption basically means your calls are “stored” in a “lockbox.” We place the recording in the box, and then you access it from your side. One way in, one way out.
Call recordings are super safe with MeetingOne – you can be sure of that.
(Note: Call Recordings are deleted after 30 days.)
Conclusion
While it’s hard to dispute that reliability will remain the primary reason organizations use PSTN providers, conference call security is one aspect that should be considered just as valuable. Hackers and call snoopers aren’t going to just give up and stealing information. That’s why MeetingOne believes in having the best conference call security in the industry!
If you hold confidential calls and need a secure audio conferencing option, MeetingOne is built to serve your organization.
All of the features mentioned come with every AudioOne account! You get layered conference call security at a reasonable cost no matter how big or small your company is!
Learn more about AudioOne, or if you’re interested in trying out the platform, start a 30-day FREE trial now!


















